Tag Archive: Cybersecurity
December 1, 2023 / by Marco / business, compliance, Cybersecurity, entrepreneur, ethics, Legal, recruitment

CHALLENGES FACED BY A LEGAL COMPANY?
Legal companies play a vital role in society, providing essential services ranging from representing individuals and businesses to advocating for justice and compliance with the law. This article will break into common challenges encountered by legal firms as they navigate the complex legal landscape. These hurdles encompass the ever-evolving nature of the legal profession and […]
read more
CYBERSECURITY TIPS FOR BUSINESS PHONES
When most people think about cyber security, their mind is cast to their laptops and personal computers. They imagine clicking heinous links from an email scammer or downloading a file riddled with viruses. Phones can also be under threat, though. The security vulnerabilities here can be so prevalent that Olympic athletes were advised to use […]
read more
5 BEST PLACES TO LEARN ABOUT CYBERSECURITY
Whether you’re starting your own business, you’re looking to begin a career in cybersecurity, or you just want to be a bit more clued up on how to protect your data, you might be thinking of studying cybersecurity. And this is a great idea for a number of reasons! Cybersecurity is a hugely sought-after skill, […]
read moreApril 26, 2020 / by Marco / , Bundle, Business', CompTIA, Cybersecurity, deals, design, entrepreneur, Exam, Prep, website

The 3-in-1 CompTIA Cybersecurity Exam Prep Bundle for $39
Expires April 25, 2021 23:59 PST Buy now and get 86% off CompTIA Security+ (SY0-501) KEY FEATURES CompTIA Security+ is the first security certification IT professionals should earn. It establishes the core knowledge required of any cybersecurity role and provides a springboard to intermediate-level cybersecurity jobs. Hence, it is the certification globally trusted to validate […]
read moreApril 16, 2020 / by Marco / , Business', Certification, CISSP, Course, Cybersecurity, deals, Deep, design, Dive, entrepreneur, website

The CISSP Cybersecurity Certification Deep Dive Course for $19
Expires March 11, 2120 23:59 PST Buy now and get 96% off KEY FEATURES The CISSP: Certified Information Systems Security Professional Certification training package covers topics such as Access Control Systems, Cryptography, and Security Management Practices, teaching students the eight domains of information system security knowledge. Earning the CISSP proves you have what it takes […]
read moreApril 15, 2020 / by Marco / , Business', Complete, Cybersecurity, deals, design, entrepreneur, router, SYFER, VPN, website

SYFER: Complete Cybersecurity VPN Router for $152
Expires March 19, 2120 23:59 PST Buy now and get 23% off KEY FEATURES Syfer is an easy, elegant, and powerful solution for protecting your connected home or business. It encrypts your data to keep it private from ISPs, companies that collect and sell your private info, and malicious advertisers. With a system powered by […]
read moreMarch 25, 2020 / by Marco / , Bundle, Business', Certification, Complete, Cybersecurity, deals, design, entrepreneur, Training, website

The Complete Cybersecurity Certification Training Bundle for $39
Expires March 24, 2120 23:59 PST Buy now and get 98% off KEY FEATURES Digitization has conquered our lives, both personally and professionally — transporting almost all data into the vast world of internet, networks, clouds, servers, and more. And while this has made convenience and speed in terms of access, threats and risks are […]
read moreMarch 20, 2020 / by Marco / , Business', Complete, Cybersecurity, deals, design, entrepreneur, router, SYFER, VPN, website

SYFER: Complete Cybersecurity VPN Router for $169
Expires March 19, 2120 23:59 PST Buy now and get 14% off KEY FEATURES Syfer is an easy, elegant, and powerful solution for protecting your connected home or business. It encrypts your data to keep it private from ISPs, companies that collect and sell your private info, and malicious advertisers. With a system powered by […]
read moreMarch 19, 2020 / by Marco / , Bundle, Business', Certification, Cybersecurity, deals, design, entrepreneur, expert, Training, website

The Cybersecurity Expert Certification Training Bundle for $49
Expires March 03, 2120 23:59 PST Buy now and get 98% off KEY FEATURES As technology advances through time, so does its cognate threats and vulnerabilities. This is where cybersecurity becomes vital. It’s the protection of internet-connected systems including computer systems, networks, data, and more. With 46 lectures, this course bundle gives you 4 prep […]
read moreMarch 19, 2020 / by Marco / , Business', Certification, CISSP, Course, Cybersecurity, deals, Deep, design, Dive, entrepreneur, website

The CISSP Cybersecurity Certification Deep Dive Course for $59
Expires March 11, 2120 23:59 PST Buy now and get 89% off KEY FEATURES The CISSP: Certified Information Systems Security Professional Certification training package covers topics such as Access Control Systems, Cryptography, and Security Management Practices, teaching students the eight domains of information system security knowledge. Earning the CISSP proves you have what it takes […]
read moreJune 21, 2018 / by Marco / Bundle, Business', Cybersecurity, deals, design, entrepreneur, Supercharged, website

2018 Supercharged Cybersecurity Bundle for $29

KEY FEATURES
In this course, you’ll get a rock-solid insight into penetration testing techniques and learn how to test a corporate network against threats like never before. You’ll formulate pentesting strategies by relying on the most up-to-date and feature-rich Kali Linux 2, thereby learning the cutting edge in pentesting tools.
- Find out how to download & install your own copy of Kali Linux
- Properly scope & conduct the intial stages of a penetration test
- Conduct reconnaissance & enumeration of target networks
- Exploit & gain a foothold on a target system or network
- Obtain & crack passwords
- Use the Kali Linux NetHunter install to conduct wireless penetration testing
- Create proper penetration testing reports
PRODUCT SPECS
Details & Requirements
- Length of access: lifetime
- Access options: download for offline access
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Packt’s mission is to help the world put software to work in new ways, through the delivery of effective learning and information services to IT professionals. Working towards that vision, it has published over 4,000 books and videos so far, providing IT professionals with the actionable knowledge they need to get the job done–whether that’s specific learning on an emerging technology or optimizing key skills in more established tools.

KEY FEATURES
Kali Linux is the most comprehensive distribution for penetration testing and ethical hacking. This course teaches you all about the forensic analysis of computer and mobile devices that leverage the Kali Linux distribution. You’ll get hands-on, seeing how to conduct each phase of the digital forensics process: acquisition, extraction, analysis, and presentation.
- Learn how to use each tool to acquire images from the media to be analyzed
- Discuss the Autopsy forensic suite & other specialized tools
- Anaylze an Android device image using Autopsy
- Cover file carving & the recovery of deleted data
PRODUCT SPECS
Details & Requirements
- Length of access: lifetime
- Access options: download for offline access
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Marco Alamanni has professional experience working as a Linux system administrator and Information Security analyst in banks and financial institutions.
He holds a BSc in Computer Science and an MSc in Information Security. His interests in information technology include ethical hacking, digital forensics, malware analysis, Linux, and programming, among other things. He also collaborates with IT magazines to write articles about Linux and IT security.
He has used Kali Linux on various occasions to conduct incident response and forensics in his professional activity, besides using it for penetration testing purposes. He is also the author of “Kali Linux Wireless Penetration Testing Essentials” published by Packt Publishing.

KEY FEATURES
This book will illustrate how and why you should learn Python to strengthen your analysis skills and efficiency as you creatively solve real-world problems. Each chapter walks you through a forensic artifact and one or more methods to analyze the evidence. With all this knowledge, you can rapidly develop and deploy solutions to identify critical information and fine-tune your skill set as an examiner.
- Discover how to perform Python script development
- Update yourself by learning the best practices in forensic programming
- Build scripts through an iterative design
- Explore the rapid development of specialized scripts
- Understand how to leverage forensic libraries developed by the community
- Conduct effective & efficient investigations through programmatic pre-analysis
- Discover how to transform raw data into customized reports and visualizations
PRODUCT SPECS
Details & Requirements
- Length of access: lifetime
- Access options: download for offline access
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Packt’s mission is to help the world put software to work in new ways, through the delivery of effective learning and information services to IT professionals. Working towards that vision, it has published over 4,000 books and videos so far, providing IT professionals with the actionable knowledge they need to get the job done–whether that’s specific learning on an emerging technology or optimizing key skills in more established tools.

KEY FEATURES
Mobile phone forensics is the science of retrieving data from a mobile phone under forensically-sound conditions. In this book, you’ll deep dive into mobile forensics techniques in iOS 8-9.2, Android 4.4-6, and Windows Phone devices. You’ll learn the latest open source and commercial mobile forensics tools, enabling you to analyze and retrieve data effectively.
- Discover the new features in practical mobile forensics
- Understand the architecture & security mechanisms present in iOS and Android platforms
- Identify sensitive files on the iOS & Android platforms
- Set up the forensic environment
- Extract & recover data on the iOS & Android platforms
- Understand the forensics of Windows devices
- Explore various third-party application techniques & data recovery techniques
PRODUCT SPECS
Details & Requirements
- Length of access: lifetime
- Access options: download for offline access
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Packt’s mission is to help the world put software to work in new ways, through the delivery of effective learning and information services to IT professionals. Working towards that vision, it has published over 4,000 books and videos so far, providing IT professionals with the actionable knowledge they need to get the job done–whether that’s specific learning on an emerging technology or optimizing key skills in more established tools.

KEY FEATURES
Security flaws and new hacking techniques emerge practically overnight, and security professionals need to keep up. With this practical guide, you’ll learn how to build your own virtual pentesting lab environments to practice and develop your security skills.
- Learn proven security testing & penetration testing techniques
- Build multi-layered complex architectures to test the latest network designs
- Apply a professional testing methodology
- Determine whether there are filters between you & the target and how to penetrate them
- Deploy & find weaknesses in common firewall architectures
- Learn advanced techniques to deploy against hardened environments
PRODUCT SPECS
Details & Requirements
- Length of access: lifetime
- Access options: download for offline access
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Packt’s mission is to help the world put software to work in new ways, through the delivery of effective learning and information services to IT professionals. Working towards that vision, it has published over 4,000 books and videos so far, providing IT professionals with the actionable knowledge they need to get the job done–whether that’s specific learning on an emerging technology or optimizing key skills in more established tools.

KEY FEATURES
If penetration testing is a battle then Metasploit is the deadliest and stealthiest weapon to use. Metasploit is a feature-rich tool that can be integrated with third-party tools easily. This course is a complete guide to numerous techniques using real-time demonstrations to sharpen your skills and give you a clear understanding of the complete framework.
- Learn how to scan for vulnerabilities in the target or network
- Build standalone payloads using msfencode
- Exploit operating systems
- Explain how Armitage can be used to leverage the powers of Metasploit over a GUI interface
PRODUCT SPECS
Details & Requirements
- Length of access: lifetime
- Access options: download for offline access
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Abhinav Singh is a young Information Security specialist from India. He has a keen interest in the field of hacking and network security and has adopted it as his full-time profession. He is also the author of Metasploit Penetration Testing Cookbook, Packt Publishing. He is an active contributor to the SecurityXploded community. Abhinav’s works have been quoted in several security and technology magazines and portals.

KEY FEATURES
There are more web applications than ever these days and a greater need than ever to make them secure. Web penetration testing is the use of tools and code to attack a website or web app to assess its vulnerabilities to external threats. This course will walk you through the web application penetration testing methodology, showing you how to write your own tools with Python for every main activity in the process.
- Get an overview of the web application penetration testing process & the tools used
- Learn HTTP & how to interact w/ web applications using Python and the Requests library
- Test tools against a vulnerable web application
PRODUCT SPECS
Details & Requirements
- Length of access: lifetime
- Access options: download for offline access
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Christian Martorella has been working in the field of Information Security for the last 16 years, and is currently working as Principal Program Manager in the Skype Product Security team at Microsoft. Christian’s current focus is on software security and security automation in a Devops world.
Before this, he was the Practice Lead of Threat and Vulnerability for Verizon Business, where he led a team of consultants in delivering security testing services in EMEA for a wide range of industries including Financial Services, Telecommunications, Utilities, and Government.
Christian has been exposed to a wide array of technologies and industries, which has given him the opportunity to work in every possible area of IT security and from both sides of the fence, providing him with a unique set of skills and vision on Cyber Security.
He is the co-founder and an active member of Edge-Security team, who releases security tools and research. Christian has contributed to open source security testing and information gathering tools such as OWASP WebSlayer, Wfuzz, theHarvester, and Metagoofil, all included in Kali, the penetration testing Linux distribution.
Christian presented at Blackhat Arsenal USA, Hack.Lu, What The Hack!, NoConName, FIST Conferences, OWASP Summits, OWASP meetings (Spain, London, Portugal, and Venice), and Open Source Intelligence Conference (OSIRA). In the past, Christian has organized more than 20 FIST Conferences in Barcelona, providing a forum for professionals and amateurs interested in Security Testing. Christian holds a Master’s degree in Business Administration from Warwick Business School, and multiple security certifications such as CISSP, CISM, CISA, OPSA, and OPST.

KEY FEATURES
Kali Linux is a Debian-based Linux distribution designed for digital forensics and penetration testing. This book will take you on a journey where you’ll learn to master advanced tools and techniques to conduct wireless penetration testing with Kali Linux. By the end of the book, you’ll have mastered using Kali Linux for wireless security assessments and become a more effective penetration tester and consultant.
- Fingerprint wireless networks w/ the various tools available in Kali Linux
- Learn various techniques to exploit wireless access points using CSRF
- Crack WPA/WPA2/WPS & crack wireless encryption using Rainbow tables more quickly
- Perform man-in-the-middle attacks on wireless clients
- Understand client-side attacks, browser exploits, Java vulnerabilities, & social engineering
- Develop advanced sniffing & PCAP analysis skills to extract sensitive information such as DOC, XLS, and PDF documents from wireless networks
- Use Raspberry PI & OpenWrt to perform advanced wireless attacks
- Perform a DOS test using various techniques & tools
PRODUCT SPECS
Details & Requirements
- Length of access: lifetime
- Access options: download for offline access
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Packt’s mission is to help the world put software to work in new ways, through the delivery of effective learning and information services to IT professionals. Working towards that vision, it has published over 4,000 books and videos so far, providing IT professionals with the actionable knowledge they need to get the job done–whether that’s specific learning on an emerging technology or optimizing key skills in more established tools.

KEY FEATURES
This book has the most advaned tools and techniques to reproduce the methods used by sophisticated hackers to make you an expert in Kali Linux. From being introduced to Kali’s top tools to finding your way around your target network to proving that vulnerabilities are real and exploitable, this book will help you cover all the bases of modern pentesting.
- Set up Kali Linux for pentesting
- Map & enumerate your Windows network
- Exploit several common Windows network vulnerabilities
- Attack & defeat password schemes on Windows
- Debug & reverse-engineer Windows programs
- Recover lost files, investigate successful hacks & discover hidden data in innocent-looking files
- Catch & hold admin rights on the network, and maintain backdoors on the network after your initial testing is done
PRODUCT SPECS
Details & Requirements
- Length of access: lifetime
- Access options: download for offline access
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Packt’s mission is to help the world put software to work in new ways, through the delivery of effective learning and information services to IT professionals. Working towards that vision, it has published over 4,000 books and videos so far, providing IT professionals with the actionable knowledge they need to get the job done–whether that’s specific learning on an emerging technology or optimizing key skills in more established tools.

KEY FEATURES
Wireshark is a widely used open source tool to profile and monitor network traffic and analyze packets. It lets you control, capture, and dynamically browse the traffic running on the organization’s network. This course will teach you about the new Wireshark 2, with enhanced features to help you protect your organization in a better way.
- Brush up on the various network protocols, OSI layers, & the role of Wireshark
- Install & configure Wireshark 2
- Experience the rich new user interface
- Focus on Wireshark’s core functionalities like Packt Analysis, IP filtering, & Protocol filters
- See how Wireshark 2 can be used to secure your network
- Use Packet Analysis for security tasks, command-line utilities, & tools that manage trace files
PRODUCT SPECS
Details & Requirements
- Length of access: lifetime
- Access options: download for offline access
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Alex Kuzmenko (https://www.linkedin.com/in/kuzmenkoa), the author of this course, has more than 16 years of engineering hands-on experience in Telecom field. He has used Wireshark for mobile network integration, testing, and troubleshooting for more than 5 years in his job in Ericsson, North America. He also had 6 years of technical training experience preparing and conducting courses related to mobile packet networks in Europe and Asia.
January 12, 2018 / by Marco / Business', Cybersecurity, deals, design, entrepreneur, Ethical, hacker, subscription, Training, website, Yr
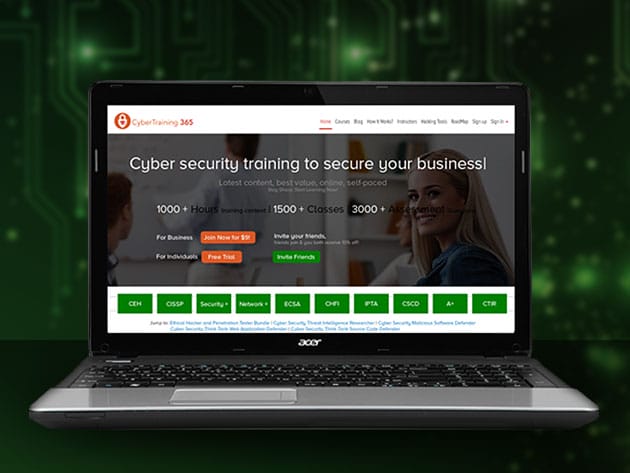
CyberSecurity Ethical Hacker Training: 1-Yr Subscription for $99
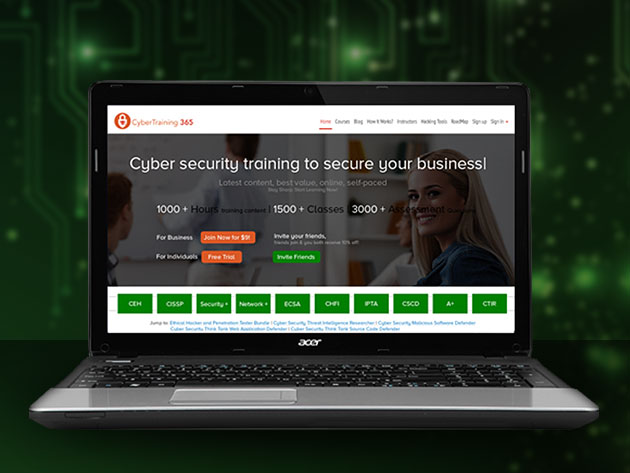
KEY FEATURES
The digital space is more crowded than ever yet the vast majority lack even basic cyber security skills. You can advance your skills, however, through this training, helping you to identify the gaps in your knowledge and proceed on a self-paced track to ultimately become a fully capable ethical hacker. You can learn anywhere, anytime, on any device and earn transcripts, certificates, and achievement recognition throughout. Not only will you become confident working with cybersecurity, but you just may be ready to pursue a career in this booming industry.
- Access a library of 663 courses, 313 quizzes, & over 150 hours of training
- Learn CompTIA Security+ & Network+, ECSA, CHFI, IPTA, & more
- Identify gaps in your knowledge w/ an adaptive skill measurement that gauges your proficiency
- Understand where to start on a learning path based on your test results
- Study at your own pace
- Participate & earn transcripts, certificates, & achievement badges
- Ask world class instructors questions whenever you need
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: 1 year
- Access options: web streaming & mobile streaming
- Certification of completion included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
- To browse the course catalog, click here
Compatibility
- Internet required
THE EXPERT
Social27 is the leader in online academies. They partner with the best trainers to produce relevant and up-to-date content that is delivered in a modern social learning platform.
For more details on this course and instructor, click here.
- 1
- 2
